Modern businesses are expected to move fast, stay secure, and support flexible work environments. In my experience, many organizations struggle not because of people or processes, but because their digital tools do not work together. This is where Microsoft 365 creates real impact. When used correctly, the benefits of Microsoft 365 go far beyond email […]
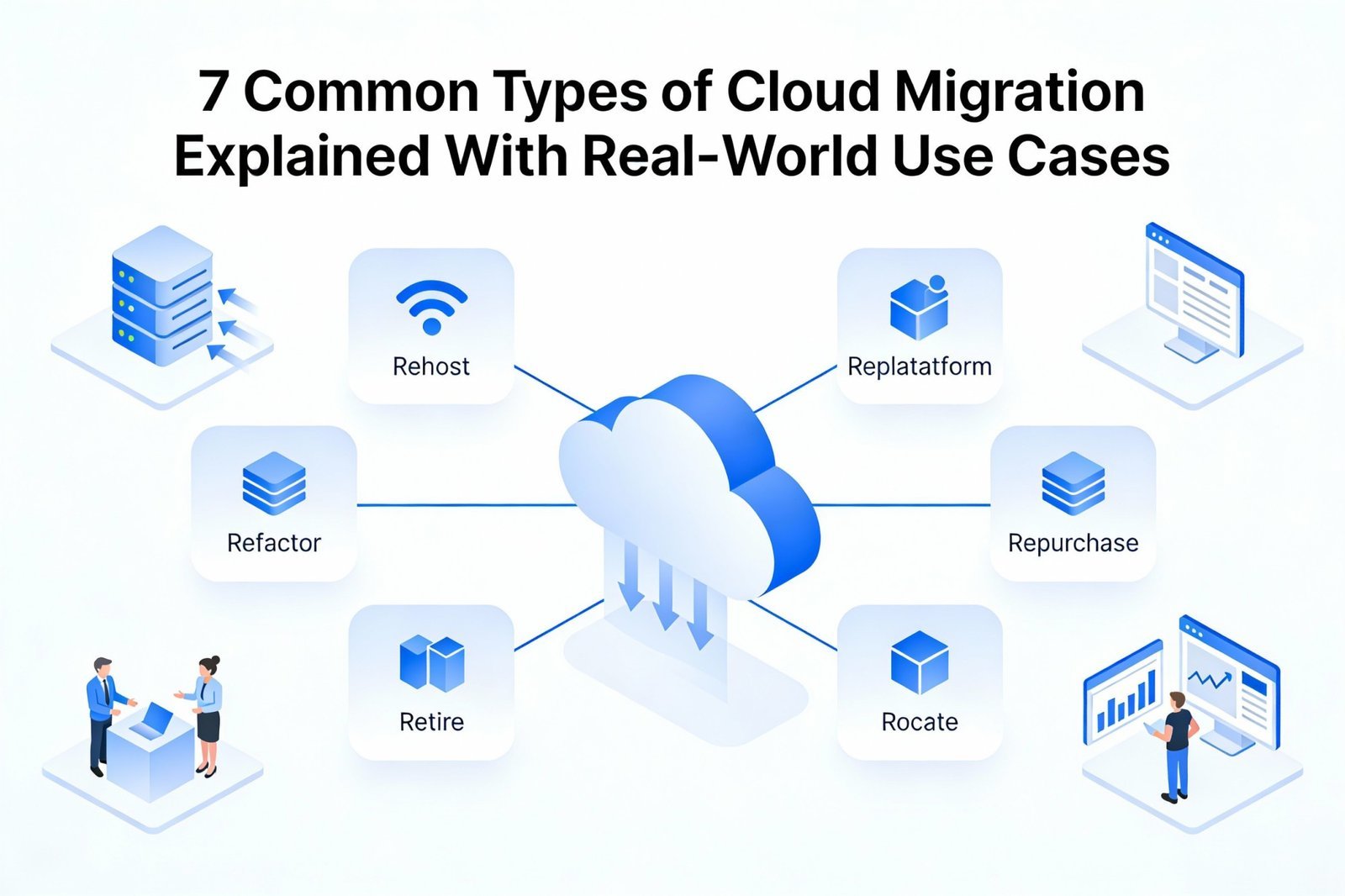
Introduction to Types of Cloud Migration In my experience working with growing businesses and large enterprises, cloud migration almost always starts with confusion. Everyone knows they need the cloud, but very few are clear about the different types of cloud migration and how each one impacts security, cost, and long term scalability. Cloud migration is […]
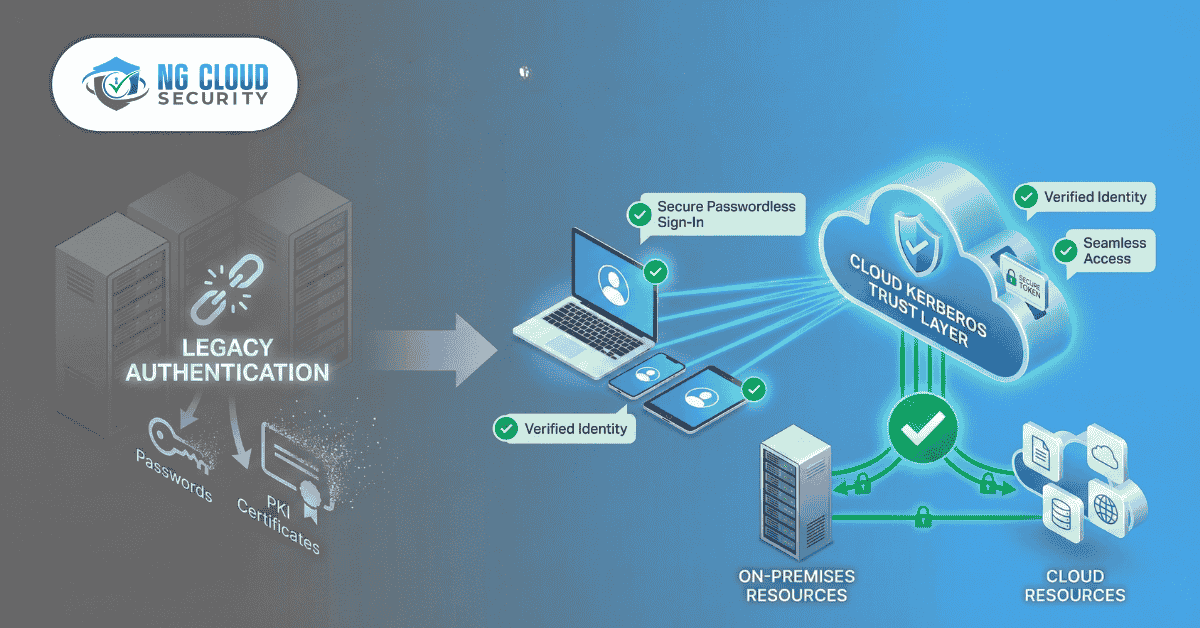
What is Windows Hello for Business? Windows Hello for Business (WHfB) is a strong authentication method built into Windows. It replaces passwords with a secure, two-factor credential. Instead of a password, users log in with a: Fingerprint Facial scan (biometrics) Device-specific PIN These credentials are asymmetric (a public/private key pair) and are bound to the […]
In today’s digital-driven business landscape, organizations manage vast amounts of sensitive information every day. Whether you are a fast-growing startup or a well-established enterprise, ensuring data protection and meeting compliance requirements are non-negotiable. Non-adherence to global and Indian cybersecurity frameworks such as ISO 27001, SOC 2, PCI-DSS, and the Digital Personal Data Protection (DPDP) Act […]
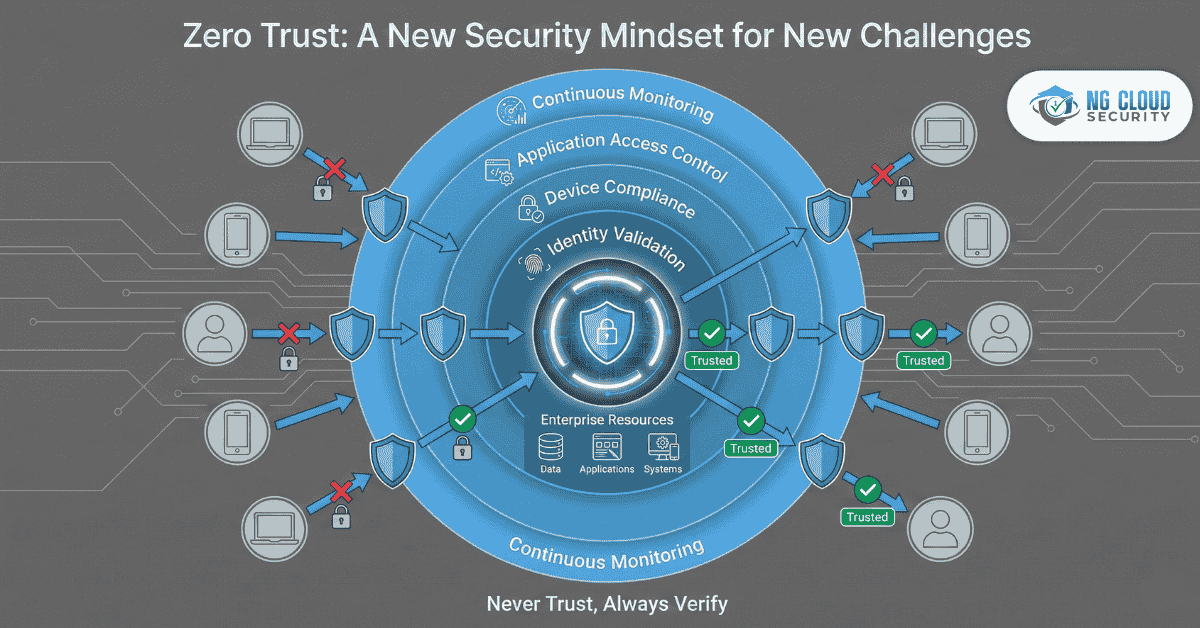
In today’s digital-first world, cyber threats are no longer limited to external attacks. Insider threats, credential theft, and supply chain vulnerabilities have become equally dangerous. Traditional perimeter-based security models that rely on the concept of “trust but verify” are proving inadequate. That’s where Zero Trust security solutions come in — a revolutionary approach that challenges […]
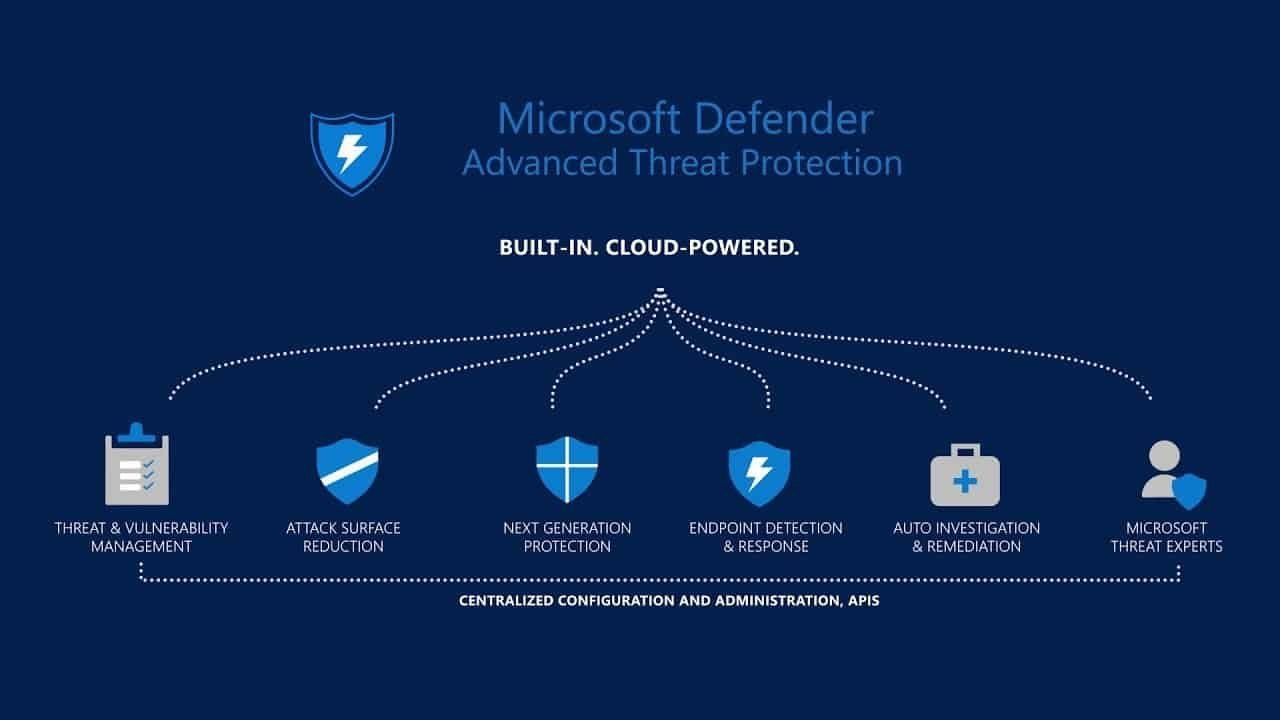
Top Endpoint Security Threats and How to Stop Them in 2026 remain a critical concern for businesses as cybercriminals evolve. With hybrid work, mobile devices, and cloud integration, endpoints are among the most targeted attack surfaces. NG Cloud Security helps organizations stay ahead using Microsoft Defender for Endpoint. In 2026, endpoint security stands at the […]
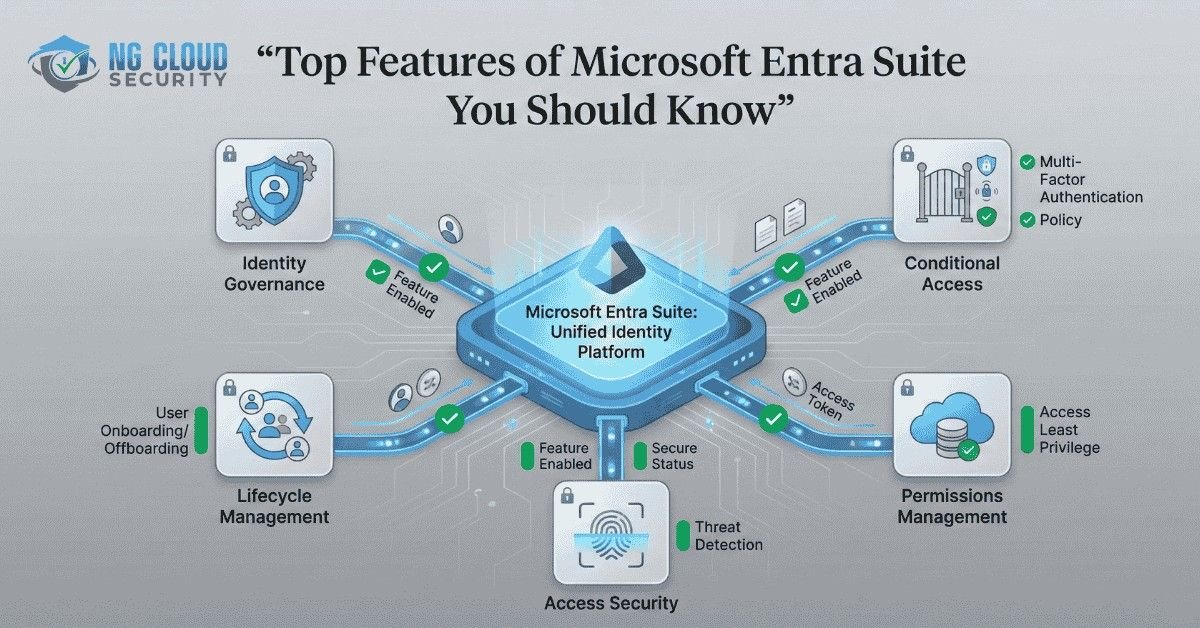
In today’s digital landscape, managing identity and access securely is more critical than ever. As organizations expand across cloud and hybrid environments, the need for a unified identity management solution becomes paramount. Microsoft Entra Suite has emerged as a powerful solution for modern identity and access management (IAM), offering enterprises a way to protect users, […]
In today’s fast-evolving cyber landscape, organizations face threats that are more advanced and harder to detect than ever before. Traditional security solutions that work in isolation often fail to provide comprehensive visibility across an organization’s IT environment. This is where XDR security solutions step in to bridge the gap, and Microsoft has emerged as a […]
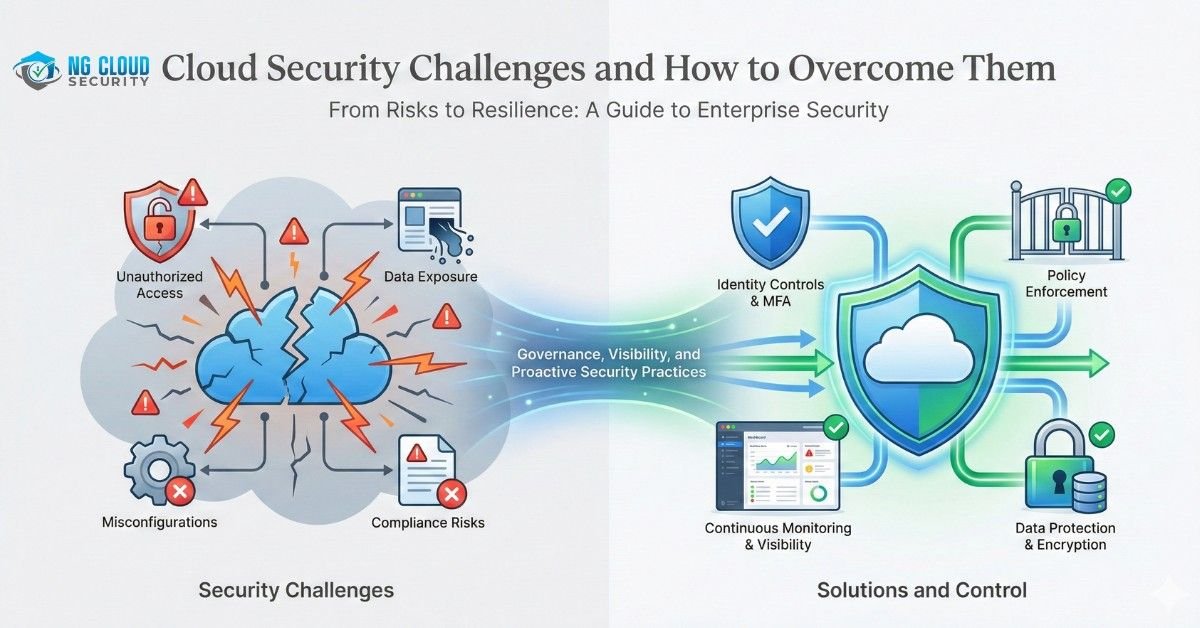
In today’s digital-first world, businesses rely heavily on cloud infrastructure for flexibility,scalability, and cost efficiency. While the cloud offers countless advantages, it also comes withrisks that organizations cannot afford to ignore. Cloud Security Challenges are among the mostpressing issues in IT, often putting sensitive data and critical systems at risk if left unaddressed.To build trust […]
In today’s digital-first world, the biggest risks to data often come from within—not just from hackers or malicious outsiders. Insider threats, whether intentional or accidental, are rising rapidly across industries. This is where Microsoft 365 Insider Risk Management (IRM) becomes a powerful solution for organizations of all sizes. This blog breaks down what Insider Risk […]