In today’s digital landscape, Microsoft 365 E5 Identity is essential for organizations looking to enhance their security measures. This suite goes beyond basic access control to provide advanced features that protect identities and resources. With its robust tools, businesses can strengthen their security posture and ensure that only authorized users have access to sensitive data. […]
In today’s world, Microsoft 365 E5 Compliance is essential for businesses of all sizes. Compliance is not just a requirement; it is a crucial part of effective business operations. Organizations must protect sensitive data, ensure regulatory adherence, and maintain trust with their customers. The Microsoft 365 E5 suite provides powerful tools to help manage these challenges […]
If your cloud environment is live, that’s a great first step. But have you checked if it’s secure, meets compliance needs, and is aligned with the Zero Trust model? Many organizations move fast into the cloud without checking for security gaps or compliance issues. An Azure Cloud Security Assessment helps spot those issues before they […]
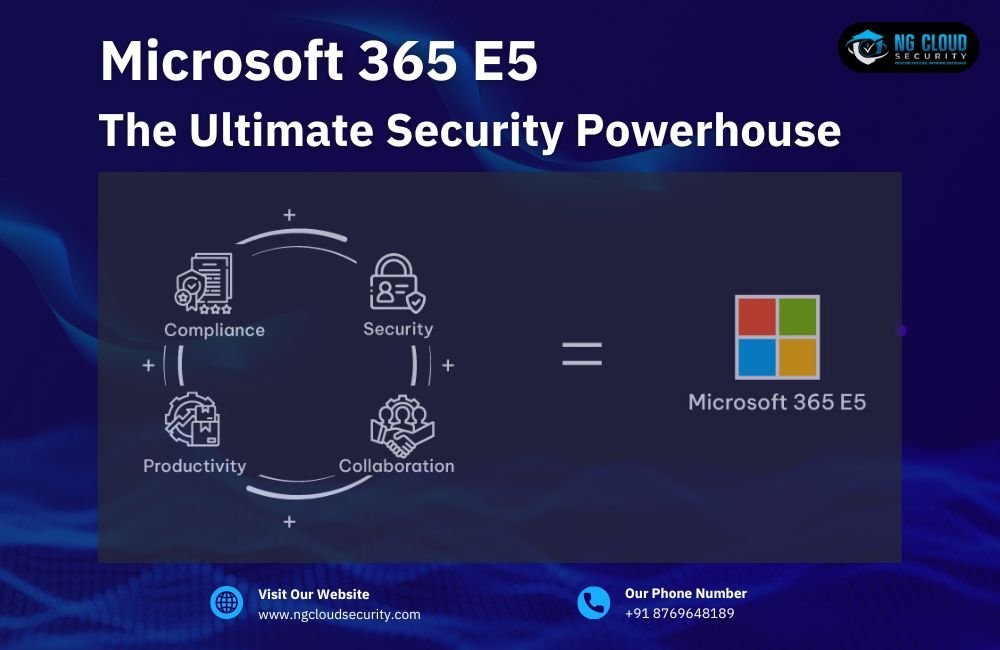
Microsoft 365 E5 is more than just a productivity tool. It’s a powerful, enterprise-level security suite designed to protect your digital environment from end to end. With threats becoming more complex and frequent, businesses need more than basic protection. Microsoft 365 E5 brings advanced security, identity management, and threat detection tools under one license — […]
Empowering Growth, Security, and Productivity with Expert Support In today’s fast-paced digital world, businesses need more than just powerful tools—they need the right support to use them effectively. Microsoft 365 is one of the most comprehensive productivity suites available, offering cloud-based collaboration, security, and productivity tools. But without proper management, businesses often fail to tap […]
Introduction The integration of Artificial Intelligence (AI) into cybersecurity has revolutionized both offensive and defensive strategies. While AI enhances threat detection and response capabilities, it also empowers cybercriminals to execute more sophisticated attacks. This article delves into the dual role of AI in cybersecurity, exploring its applications in both cyberattacks and defense mechanisms. The Rise […]
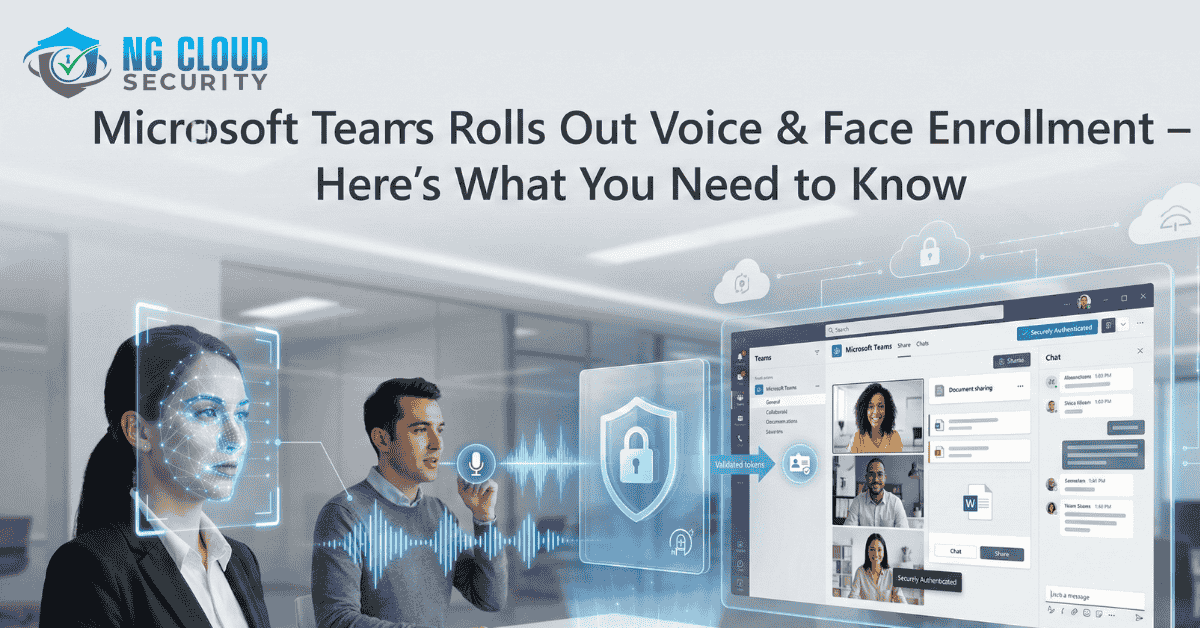
Empowering Secure, Intelligent Collaboration Experiences 🔍 What’s New? Microsoft is introducing Voice and Face Enrollment in Microsoft Teams—a smart feature that improves audio clarity, speaker recognition, and meeting accuracy, especially in setups with Microsoft Teams Rooms devices. This AI-driven feature supports: Speaker attribution (who is speaking, when) Improved Microsoft Copilot performance in meetings Reduction of […]
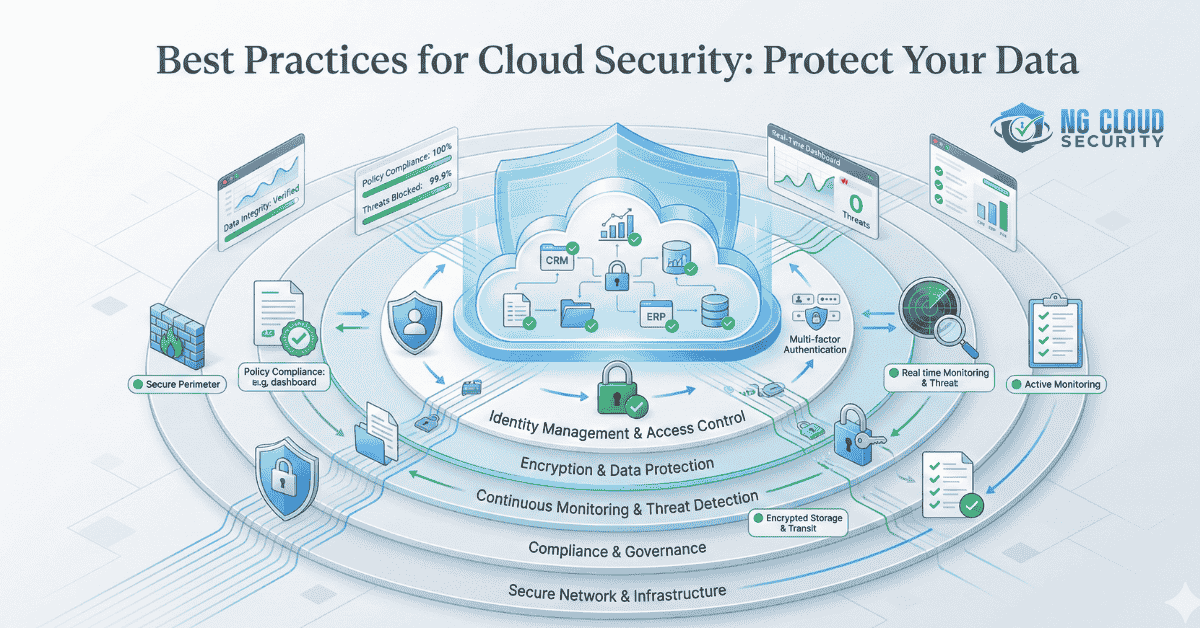
In today’s digital age, cloud computing has become an essential component for businesses and individuals alike. While cloud services offer scalability, cost-efficiency, and accessibility, they also introduce significant security challenges. Cyber threats, data breaches, and compliance risks necessitate the implementation of robust cloud security practices. This article provides an in-depth exploration of the best practices […]
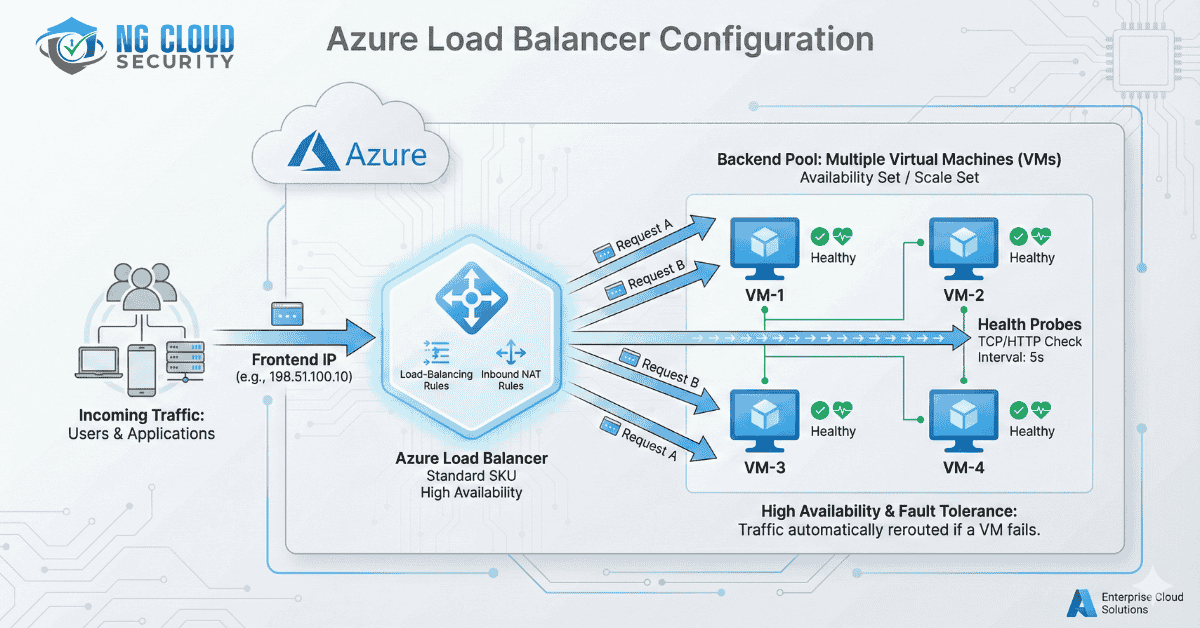
Load balancing refers to efficiently distributing incoming network traffic across a group of backend servers or resources. Azure Load Balancer operates at layer 4 of the Open Systems Interconnection (OSI) model. It’s the single point of contact for clients. Load balancer distributes inbound flows that arrive at the load balancer’s front end to backend pool […]