Top Endpoint Security Threats and How to Stop Them In today’s digital landscape, endpoint security has become a critical concern for organizations worldwide. With cyber threats evolving rapidly, businesses must stay vigilant and proactive in protecting their networks. NG Cloud Security, a leading provider of cloud security solutions, offers comprehensive services to safeguard enterprises against these […]
In today’s digitally-driven world, email remains one of the most widely used communication channels for both businesses and individuals. While emails offer convenience and efficiency, they are also a prime target for cybercriminals. One of the most prevalent threats is phishing attacks—deceptive attempts by attackers to trick users into revealing sensitive information suchas passwords, credit […]
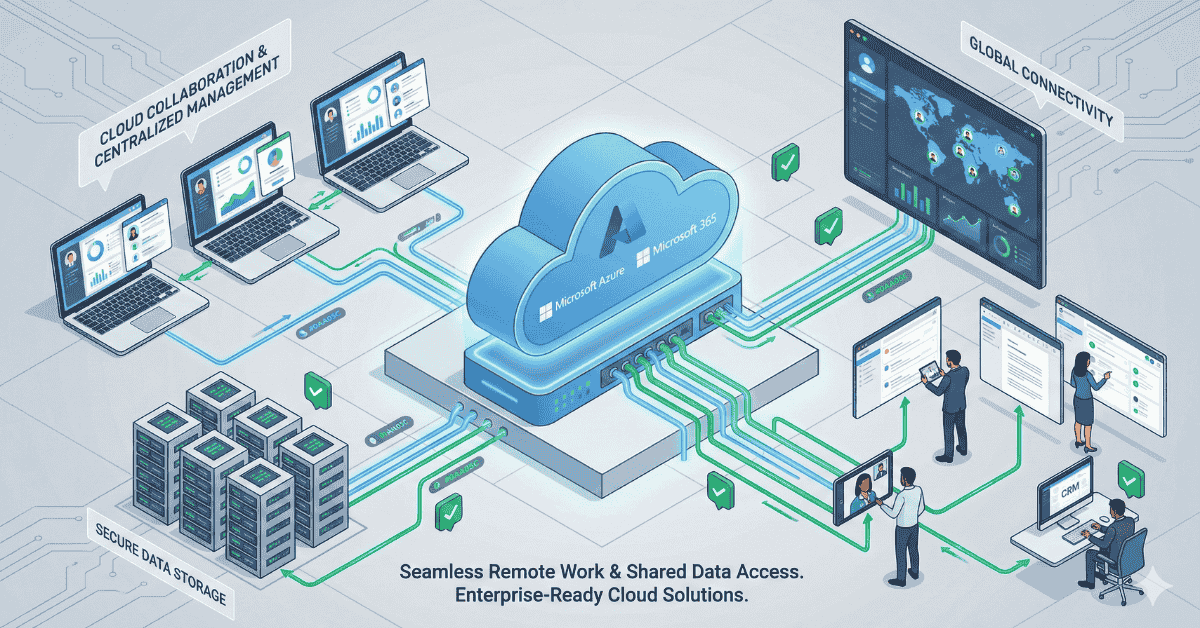
Businesses across India are embracing the cloud to stay agile, efficient, and future-ready. Whether it’s about scaling operations, improving collaboration, or strengthening data security, cloud technology has become the backbone of digital transformation. However, the migration process itself can be complex — involving risks of downtime, data loss, and security breaches ifnot executed correctly. That’s […]
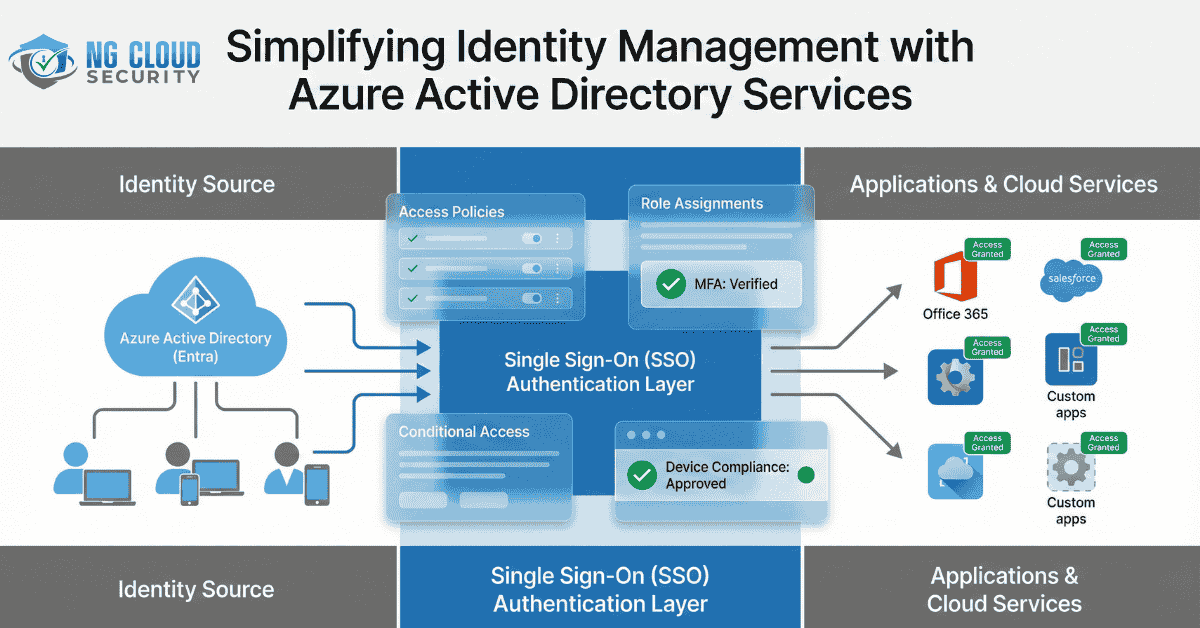
Simplifying Identity Management with Azure Active Directory Services In today’s cloud-driven business environment, secure identity and access management have become essential. As organizations embrace hybrid and multi-cloud infrastructures, the need for centralized identity control, enhanced user authentication, and secure access to corporate resources has grown significantly. Azure Active Directory Services (Azure AD) has emerged as […]
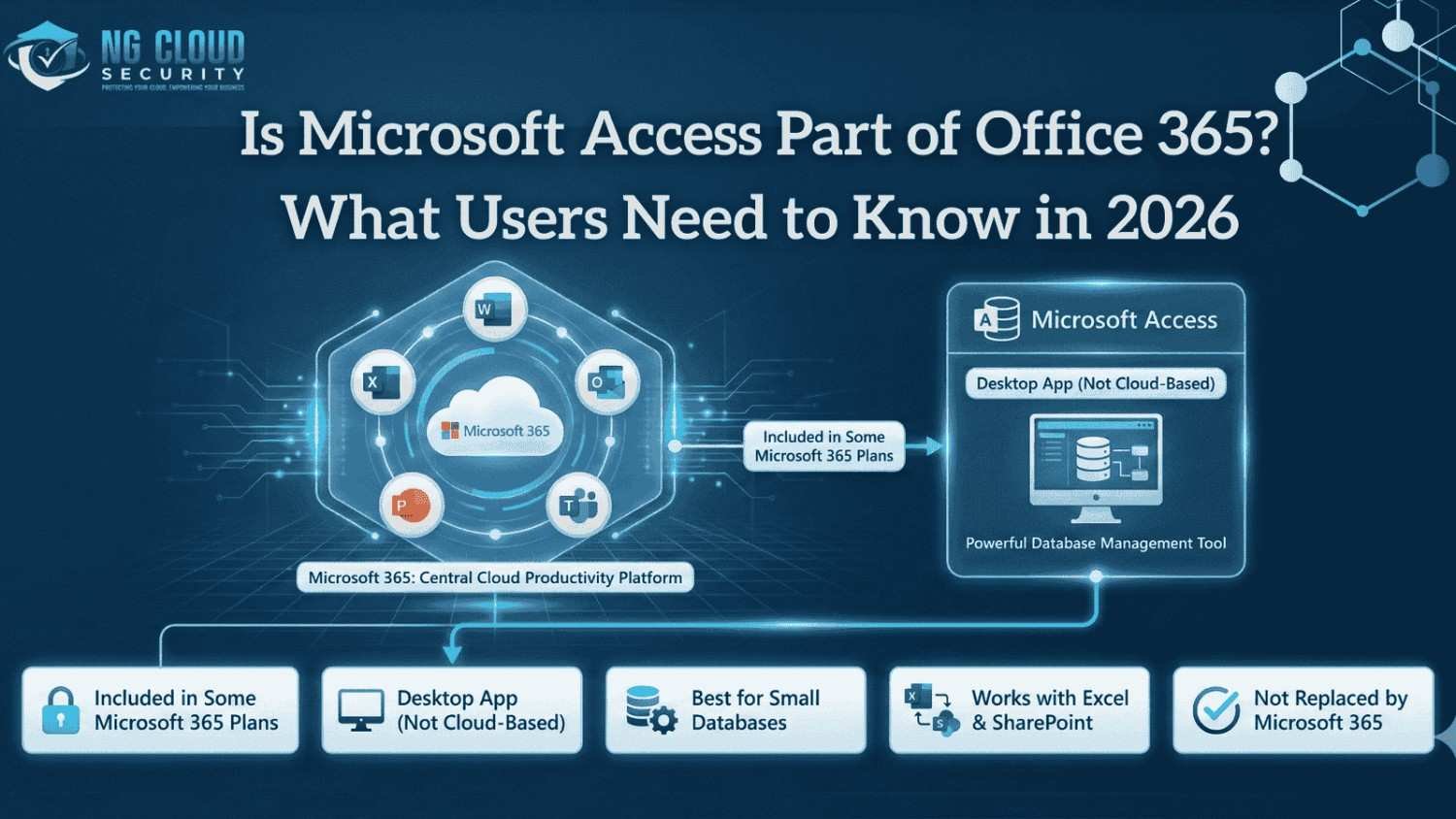
In my experience working with organizations adopting Microsoft 365, one question keeps coming up again and again. Is Microsoft Access part of Office 365, and does it still make sense to rely on it in a cloud first environment? The confusion is understandable. Microsoft 365 has evolved rapidly, focusing more on cloud services, browser based […]
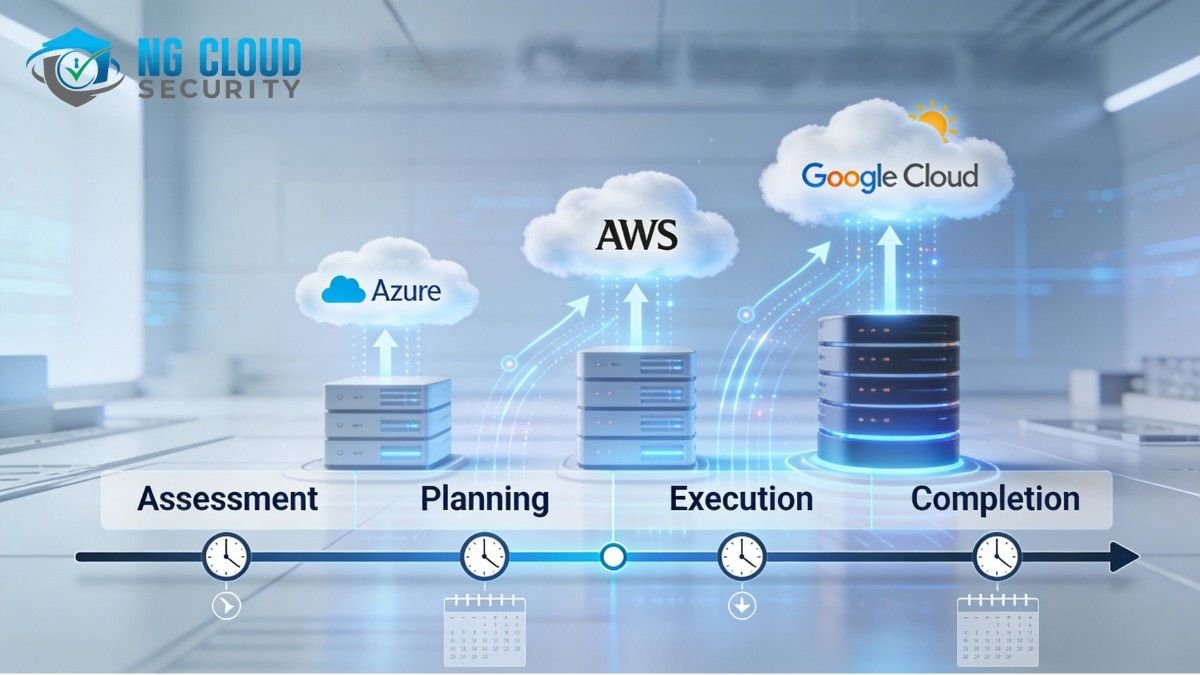
How Long Does Cloud Migration Take for Enterprises When business leaders ask me how long does cloud migration take, my honest answer is always it depends. In enterprise environments, cloud migration is not a single task. It is a structured transformation that impacts infrastructure, applications, security, and operations. In my experience, organizations that first understand the different […]
Introduction to Endpoint Security for Mac When people talk about cybersecurity, Mac devices are often assumed to be safer by default. In my experience, that assumption creates more risk than protection. Mac endpoints are now widely used in enterprises, remote teams, and leadership roles, making them a prime target for modern attacks. This is where […]
One of the most common questions I hear from business owners today is simple but important. How does zero trust work and why is it becoming the foundation of modern cybersecurity. From my experience working with organizations moving to cloud and hybrid environments, traditional security models no longer match how businesses actually operate. Users work […]
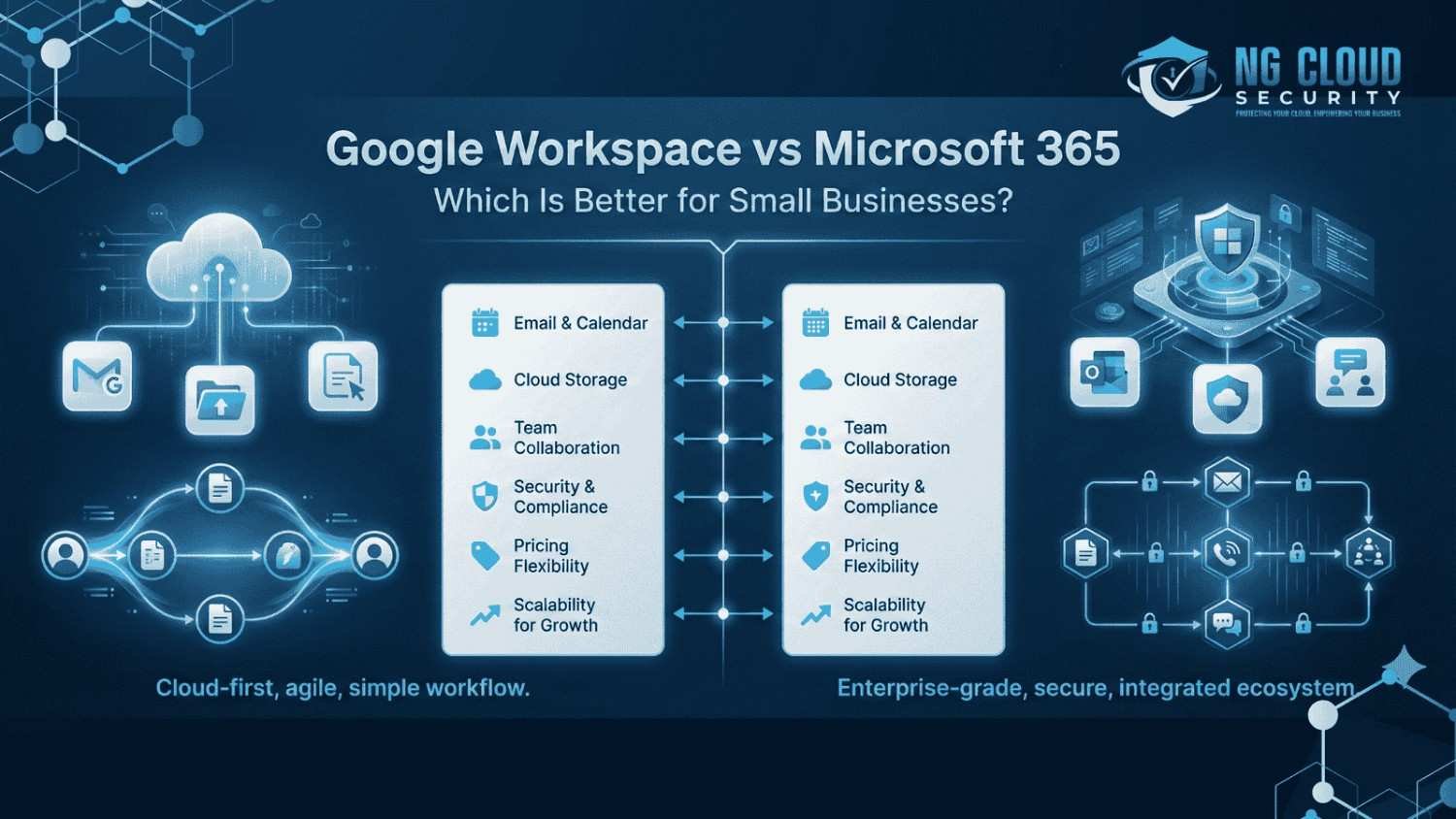
When small business owners ask me to compare productivity platforms, the discussion usually comes down to google workspace vs microsoft 365 for small business. I have seen both platforms used across different industries, and the right choice often depends on how a business works today and how it plans to grow. Productivity tools are no […]
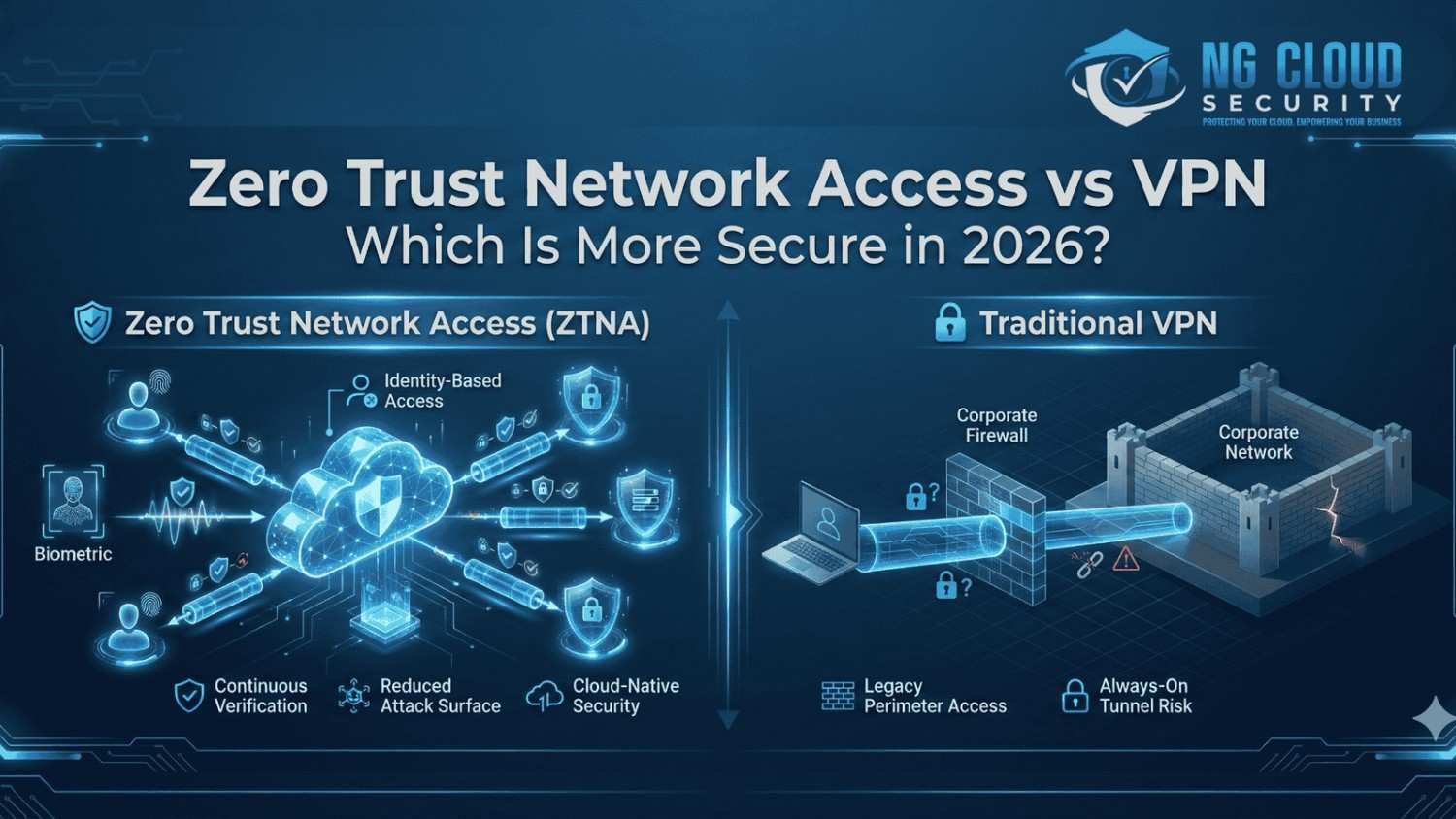
Over the last few years, I have seen a major shift in how organizations think about remote access security. As cloud adoption grows and workforces become more distributed, the conversation around zero trust network access vs vpn has become more important than ever. In 2026, security teams are no longer asking which solution is easier […]